What is Shodan:
Shodan is a search engine that allows researchers to explore and discover a wide range of devices that are connected to the internet, where they are located and who is using them. Shodan is a very powerful reconnaissance tool that can be used to see the bigger picture of internet-connected/public-facing devices such as Smart TVs, refrigerators, Webcams, SCADA and much more [1]. Shodan has servers located around the world that crawl the internet 24/7 to provide the latest internet connected device intelligence. Using this intelligence can tell you a wide array of information, like where devices are located geographically, what types of technology and versions are present on the devices discovered.
Why use Shodan:
Shodan is of particular use for security research that is focused around internet connected devices such as Internet of Things (IoT). The number of devices connected to the internet has surpassed 26+ billion worldwide according to Statista consumer data reports conducted in 2018 [2]. As IoT devices become more popular in our daily lives, we can expect these numbers to increase drastically over the next several years. The state of IoT connected devices are projected to grow 10% according to” iot-analytics” global research market breakdown [3].
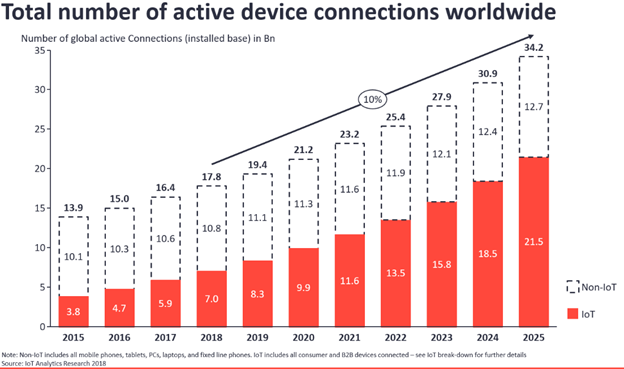
As we see internet-connected devices increase, Shodan can be a great reconnaissance tool for researchers and organizations alike. This search engine can help organizations discover internet-connected devices and provide global insight into an organization attack surface. Also, with Shodan’s vast internet-scale data researchers can conduct large scale research quickly. This is one of my go-to tools when conducting attack surface profiling.
Getting Started with Shodan
Basic Shodan UI Overview
The new Shodan UI is broken down into two primary columns, the left column focuses on several core areas such as total results returned, top ports, organizations, products and operating systems discovered.
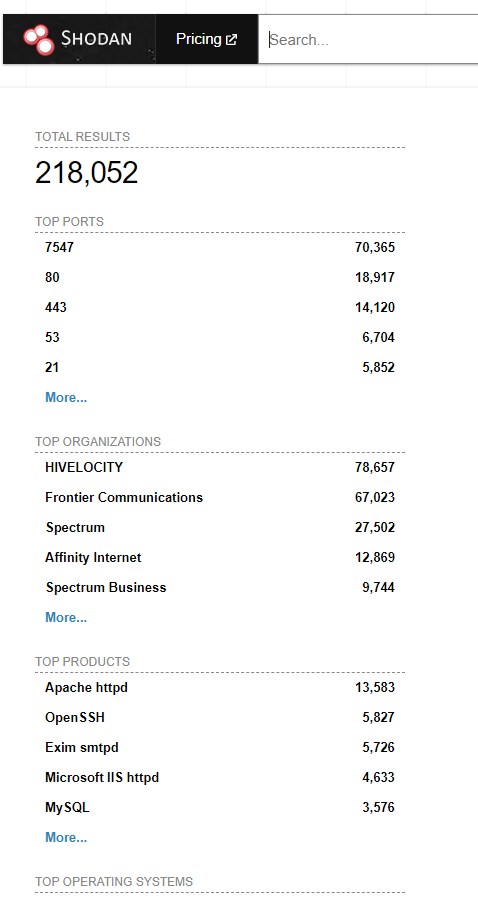
The center column focuses on the data returned based on the search query filter. This area brings back the specific details related to returned results such as the IP address, location, technology, organization, certificates, response codes and other important information.
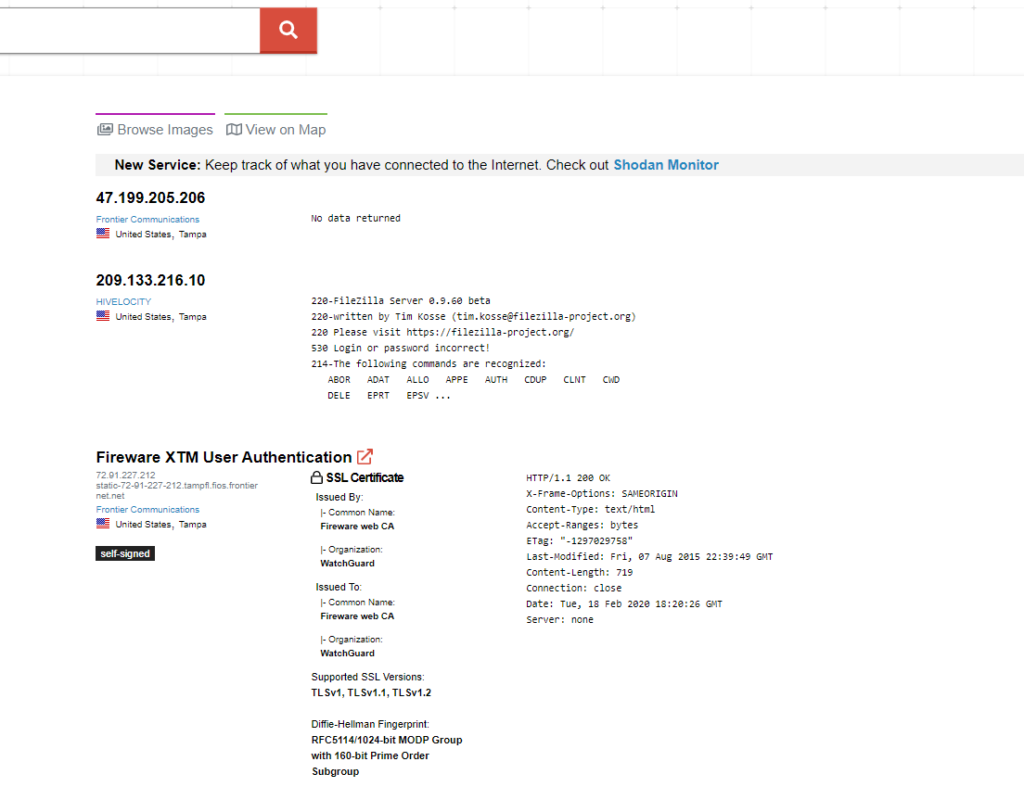
If you click on a specific IP address/hostname within Shodan, it will drill into a full information view that breaks down the raw data into sections based on General Information, Web Technologies, Vulnerabilities, Open Ports, etc. The Shodan website UI is very intuitive and user-friendly. If you have issues or want to learn more about the Shodan UI you can visit the help navigate the website at the following link: https://help.shodan.io/the-basics/navigating-the-website
Shodan Basic Filters & Syntax
Below is a list of general search filters that can be utilized for the Shodan search engine. In addition to general search filters, combinations and customized search queries can be performed to get more granular search results faster. See example filters and searches area below.
Basic search filters you can use:
city:search for devices in a particular city by using the name of the citycountry:search for devices in a particular country by using 2-letter country codehttp.title:search for the title of the websitenet:search based on an IP or /x CIDRorg:search for the name of the organization that owns the IP spacegeo:discover devices via geo coordinates (longitude/latitude)hostname:searches values that match a specified hostnameos:search based on operating system discoveredport:search for exposed ports that are open and running servicesproduct:search for the name of a product or technology stack
“All filter references can be found documented on the Shodan website at [5]: https://beta.shodan.io/search/filters.”
Example Filters & Searches
- Discover Apache products:
product:Apache
Discover Webcams:Server: SQ-WEBCAM - Discover Windows XP Operating System in San Francisco:
city:"San Francisco" os:"Windows XP" - Discover RDP exposed in New Orleans:
city:"New Orleans" port:3389 - Discover exposed Citrix NetScaler’s:
http.waf:”Citrix NetScaler” - Discover Elastic Search host:
port:9200 all:"indices" all:"production" - Discover Routers with Default Credentials:
"admin+1234"
Report & Data Exports: You can create reports or export your search results in Shodan by clicking on “create report” or “download results” to export data based on your needs. The download results allow you to export data as CSV, JSON or XML.
New Features:
- New Beta Search Engine: Shodan beta search engine adds additional intelligence across the search platform. It gives more data-drive view of the technology and vulnerabilities that could be impacted on the devices discovered in a newer UI interface [6].
- Shodan Monitor: Shodan network monitor allows an organization to keep track of the devices that they have exposed to the internet. You can easily setup monitoring and notifications to show complete visibility into what you have connected [7].
- Shodan Exploits: Shodan exploits is a search engine that pulls known exploits back to from several sources such as ExploitDB and Metasploit in an easy to navigate UI [8].
References:
- [1]. You should also check out shodan at https://www.shodan.io/, and the blog at https://blog.shodan.io.
- [2]. Statista, 2019 reporting - https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/
- [3]. State of the IoT 2018: Number of IOT devices connected and accelerating growth metrics - https://iot-analytics.com/state-of-the-iot-update-q1-q2-2018-number-of-iot-devices-now-7b/
- [4]. Shodan help navigate the website - https://help.shodan.io/the-basics/navigating-the-website
- [5]. Shodan Filter references - https://beta.shodan.io/search/filters
- [6]. Shodan Beta Search - https://monitor.shodan.io/
- [7]. Shodan Monitor - https://beta.shodan.io/
- [8]. Shodan Exploits - https://exploits.shodan.io/