What is CyberChef?
CyberChef is a simple, intuitive web application for analyzing and decoding data without having to deal with complex tools or programming languages. It is also known as the “Cyber Swiss Army Knife” and encourages both technical and non-technical people to explore data formats, encryption and compression.
Why use CyberChef?
Data sets come in all shapes, sizes and formats in the modern digital landscape and CyberChef helps make sense of this data in an easy to use web application.
How does it work?
As stated above the CyberChef web application interface is very intuitive and straight forward. It takes the trivial work out of complex data sets and quickly performs a wide range of data manipulation functions called “operations”. A sequence of operations is called a “Recipe”.
Useful Operations: (CyberChef has over 300+ Operations and is rapidly growing)
| From/To Hex | Regular Expressions | Strings | All the Hashes |
| From/To Base64 | XOR Brute Force | Zip/Unzip | Script Beautify |
| URL Encode/Decode | Encrypt/Decrypt | Tar/Untar | Render Image |
| Decode Text | HTTP Request | Syntax Highlighting | Extract EXIF |
| CSV to JSON | Public Key Conversions | To/From Punycode | Extract File paths |
| JSON to CSV | Detect Filetype | Scan Embedded Files | YARA Rules |
CyberChef UI:
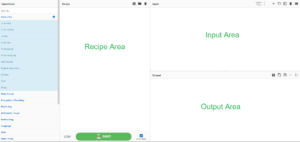
The user interface is very robust and powerful, I highly recommend hosting your own internal web app for private research and jumping in the public version to get a feel for the platform beforehand. Please see the screenshot below that outlines some of the high-level features.
CyberChef Default Key Bindings:
| Command | Shortcut (Win/Linux) | Shortcut (Mac) |
| Place cursor in search field | Ctrl+Alt+f | Ctrl+Opt+f |
| Place cursor in input box | Ctrl+Alt+i | Ctrl+Opt+i |
| Place cursor in output box | Ctrl+Alt+o | Ctrl+Opt+o |
| Place cursor in first argument field of the next operation in the recipe | Ctrl+Alt+. | Ctrl+Opt+. |
| Place cursor in first argument field of the nth operation in the recipe | Ctrl+Alt+[1-9] | Ctrl+Opt+[1-9] |
| Disable current operation | Ctrl+Alt+d | Ctrl+Opt+d |
| Set/clear breakpoint | Ctrl+Alt+b | Ctrl+Opt+b |
| Bake | Ctrl+Alt+Space | Ctrl+Opt+Space |
| Step | Ctrl+Alt+' | Ctrl+Opt+' |
| Clear recipe | Ctrl+Alt+c | Ctrl+Opt+c |
| Save to file | Ctrl+Alt+s | Ctrl+Opt+s |
| Load recipe | Ctrl+Alt+l | Ctrl+Opt+l |
| Move output to input | Ctrl+Alt+m | Ctrl+Opt+m |
| Create a new tab | Ctrl+Alt+t | Ctrl+Opt+t |
| Close the current tab | Ctrl+Alt+w | Ctrl+Opt+w |
| Go to next tab | Ctrl+Alt+RightArrow | Ctrl+Opt+RightArrow |
| Go to previous tab | Ctrl+Alt+LeftArrow | Ctrl+Opt+LeftArrow |
How will we use it in the blog post?
The focus of this blog post is to show a brief overview of how CyberChef can aid in analysis when you are attempting to decode or decipher pieces of the puzzle. Below is two example encoding techniques that are commonly utilized by attackers to evade detection.
Example 1 – Percentage-Based URL Encoding to Bypass Email Gateways in Phishing Attacks:
In this example breakdown it shows a percent-based URL encoded phishing email that is used to fool the basic URL and domain checks by perimeter devices that we often see threat actors utilize to deliver malicious payloads. We can utilize CyberChef to easily decode these phishing emails during analysis.
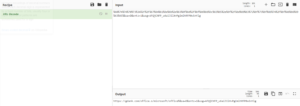
As you can see in code listed below, the true destination of the hyperlink is not immediately obvious to the untrained eye and the same holds true for many perimeter security gateways. We see the URL percent-based encoding it being utilized to redirect us to a specific URL that is encoded in the first code snippet area labeled encoded URL. After decoding the URL encoding in CyberChef we can see the malicious redirect is actually pointing to a different domain in the decoded URL section.
Encoded URL:
Hxxps://www.google.lv/url?q=%68%74%74%70%73%3A%2F%2F%67%64%61%6e%6b%2e%63%6f%6d%2F%6f%66%66%6c%63%65%2e%6f%2F%6d%69%63%72%6f%73%6f%66%74%2F%6f%66%66%69%63%65%&sa=D&sntz=1&usg=AFQjCNFP_u6aiJIlXvPgImlhRFP0w5nYlg
Decoded URL depicted in green above:
hxxps://gdank[.]com/offlce.o/microsoft/office%&sa=D&sntz=1&usg=AFQjCNFP_u6aiJIlXvPgImlhRFP0w5nYlg
Example 2 - Ransomware using PowerShell to delete Shadow Copy:
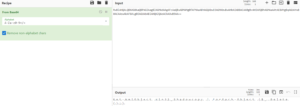
In this example breakdown you will see a tactic that is commonly used in many PowerShell related attacks to evade detection. Attackers often use base64 encoding to hide malicious attributes or strings within invoked PowerShell commands. As you can see below when the base64 is decoded you observe a command input that is utilizing PowerShell to delete shadow copies. Oftentimes these encoded PowerShell commands can be used to download malicious payloads or other nefarious actions.
Encoded PowerShell command:
[SYSMON EVENT TYPE 1 – RANSOMWARE USING POWERSHELL TO DELETE SHADOWCOPY]
Image C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
CommandLine powershell -eRwBlAHQALQBXAG0AaQBPAGIAagBlAGMAdAAgAFcAaQBuADMAMgBfAFMAaABhAGQAbwB3AGMAbwBwAHkAIAB8ACAARgBvAHIARQBhAGMAaAAtAE8AYgBqAGUAYwB0ACAAewAkAF8ALgBEAGUAbABlAHQAZQAoACkAOwB9AA==
CurrentDirectory C:\Users\port\AppData\Local\Temp\
ParentImage C:\Users\port\AppData\Local\Temp\rpr1l7q0.exe
ParentCommandLine “C:\Users\port\AppData\Local\Temp\rpr1l7q0.exe”
Decoded base64 depicted in green above:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
Conclusion
CyberChef is a powerful tool for any blue or red teamers arsenal. The possibilities with CyberChef capabilities are endless. Researchers have utilized this tool to bake up some great recipes to include breaking down group policy preference password decryption, decoding and reversing strings and character substitutions, using Yara rules with deobfuscated malicious scripts and much more. I highly recommend checking out CyberChef and trying to figure out ways it can enhance or fit into your analysis workflow.
References:
- [1]. CyberChef Project - https://gchq.github.io/CyberChef/
- [2]. Threat Actors Use Percentage-Based URL Encoding to Bypass Email Gateways - https://cofense.com/threat-actors-use-percentage-based-url-encoding-bypass-email-gateways/
- [3]. Malware examples from our friends over at BroadAnalysis - https://broadanalysis.com/